LOCK BASED PROTOCOL IN DBMS
LOCK BASED PROTOCOL
- To achieve consistency isolation is the most importent idea , locking is simplest idea to achive isolation . it first obtain a lock on a data item then preferred a desired operation and then unlock it.
- Database systems equipped with lock-based protocols use a mechanism by which any transaction cannot read or write data until it acquires an appropriate lock on it.
- to provide bettar concurrency along with isolation we use different modes of locks.
- shared mode.
- exclusive mode.
shared mode:-
in this transaction can perform read operation , any other transaction can also obtain some lock on same data at same time so it is called shared. it is denoted by lock-s(a).
exclusive mode:-
Data item can be both read as well as written.This is Exclusive and cannot be held simultaneously on the same data item. it is denoted by lock-x(A).
any other transaction cannot obtain either shared /exclusive mode lock.
Lock Compatibility Matrix –
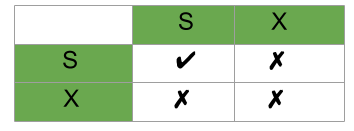

- A transaction may be granted a lock on an item if the requested lock is compatible with locks already held on the item by other
transactions. - Any number of transactions can hold shared locks on an item, but if any transaction holds an exclusive(X) on the item no other transaction may hold any lock on the item.
- If a lock cannot be granted, the requesting transaction is made to wait till all incompatible locks held by other transactions have been released. Then the lock is granted.
There are four types of lock protocol availible.
- simplistic lock protocol.
- pre-claiming lock protocol.
- two phase locking.
- strict two phase locking.
this is published by soumy sinha.
give your feedback in comment box and follow our facebook page for more information.

Comments
Post a Comment